
Cybersecurity is a preventive process that hospitals should take
more seriously as they evolve with the use of technology. There are four main
access points that hospitals and organizations should be aware of in the event
that a cyber attacker tries to breach databases and systems. This article
identifies these problems and will present the top five priorities that can help
stop 85% of all hacks.
Healthcare data is uniquely vulnerable to privacy breaches.
Government regulations forced healthcare operations to adopt electronic health
records and other advances under the Patient Protection and Affordable Care Act
even if they weren’t ready to adequately invest in security.
How prepared are you
to respond to these cyber-attacks?
A survey conducted by the American Hospital Associated showed that 75% aren’t
prepared, yet 91% said being prepared for an attack is essential to protecting
the organization.
Let’s think about Security Screening at the airport and all
the check points you go through before sitting on the plane for departure. TSA
has evolved from a one-size-fits all security screening approach to a
risk-based, intelligence-driven strategy designed to improve both security and
the passenger experience. People want to feel safe at the airport just like
people want to feel safe and germ-free at hospitals.
How are the hackers
getting through?
There are significant benefits for care delivery and organizational
efficiency from the expanded use of networked technology, internet-enabled
medical devices, and electronic data bases for clinical, financial and
administrative operations; however, these advances also increased exposure to
possible cybersecurity threats that require hospitals to evaluate and manage
new risks. Nearly 1 million new malware threats are released every day. In one
case, hackers are targeting insulin pumps, which were reported earlier this
month.
How do you manage
these unforeseen risks?
The Senior Director of the Center for Internet Security defined the
Cybersecurity trend as an equation.
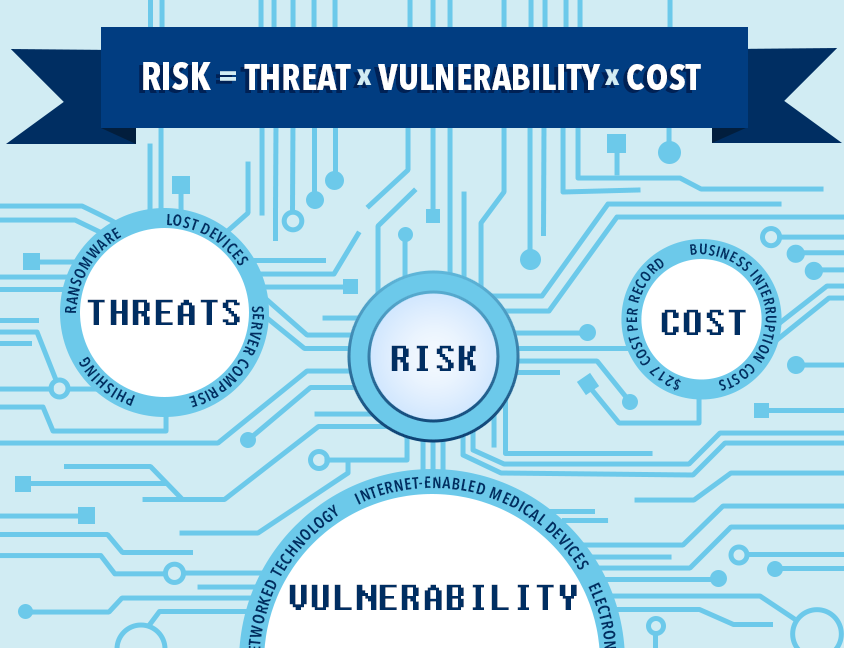
Can you afford your hospital to be shut down and patients’
data held for ransom? Before it’s too late to be sorry, consider the choices
you can make within your IT infrastructure to secure yourself against unwanted
threats.
What are the event
types for hospitals?
- Phishing – the activity of defrauding an online
account holder of personal information by posing as a legitimate company.
o
Common in the form of an email.
o
Hackers unleash data in an unsecure environment.
o
CEOs are targeted for a wire transfer or
requested bill to pay.
o Ex: Wyoming hospital hit by
phishing attack.
·
Ransomware – a typical malicious software
designed to block access to a computer system until a sum of money is paid.
o
Can be avoided by encrypting data.
o
Once hackers are in, the only options are to pay
money or restore from backups.
o
Good IT training is key!
o Ex: Hollywood hospital held to
ransom by hackers.
·
Lost Devices – over 10,000 devices lost at the
airport a year.
o
Airport donates lost devices without ever
clearing or checking if it has sensitive information on it.
o
Ex: NYC Health Center notified 1,500 patients of
PHI data breach.
· Server Comprise – there are many types of
servers in the IT world, but they all share the general purpose of connecting
information and having it stored in a centralized location.
o
SQL Inject – refers to an injection
attack of SQL statements that control web application’s database server. This
vulnerability is one of the oldest, most prevalent and most dangerous.
o Ex: Saint Francis Health System
server hacked and patient info was extracted.
These issues should be made part of the hospital’s existing
governance, risk management and business continuity framework. Proper training
for IT employees eliminates human error and can reduce the threats for
receiving and opening malware in compromised emails. Asses the security of your
physical assets and infrastructure in terms of where your data sits along with
other networks and online. Hospitals should take the steps to ensure that the cybersecurity approach adopted remains flexible and resilient to address threats that are likely to be
constantly evolving.
To understand more
about how to deal with these problems, special compliance costs, and the top
five priorities of Cyber Hygiene, please follow us on our Social Media accounts
for alerts on our next blog article!
We can help you start
today with an assessment of your security environment at your facility. Give
our experts a call and we can provide a road map for how you can make smart
investments to make your organization more secure while allowing you to focus
on serving your patients.